Frameworks
Secure Software Development Framework The Secure Software Development Framework (SSDF) is a framework published by the National Institute of Standards and Technology (NIST) and includes software development practices based on established security practices that make the software development life cycle more secure. The SSDF provides a set of software development practices that can be incorporated into an existing software development lifecycle. In-toto Attestation Framework The aim of the in-toto Attestation Framework is to define a uniform and flexible standard for software attestation. By using so-called predicates within the attestation definition, different information can be represented. Examples of this are the SLSA Provenance predicates for the two SBOM formats Software Package Data Exchange (SPDX) and CycloneDX. Supply-chain Levels for Software Artifacts Das SLSA-Framework ist ein inkrementell implementierbares Framework, wel- ches der Software Supply Chain Sicherheit dient.
Tools
Notary V2 Docker began development on Notary in 2015 and worked on it until the project was handed over to the Cloud Native Computing Foundation in 2017. Notary’s functionality includes signing and validating Open Container Initiative (OIC) artifacts. Signing and validation are done using public and private keys. The public key is stored in a container registry and the artifacts are signed with the private key. The artifact with the signature is then uploaded to the registry. The authenticity of an artifact can be verified using the registry’s public key. Sigstore Sigstore is a project of the Linux Foundation with support from many companies such as Google and RedHat. Sigstore is open source. Sigstore simplifies the signing and attestation of artifacts and the associated distribution of signatures and attestations. Sigstore mainly consists of three technologies: Cosign, Fulcio, Rekor. Cosign is a commandline tool that is responsible for signing and verifying software artifacts. Cosign also supports in-toto attestation, making it SLSA-compliant. Another functionality of Cosign is the keyless signing mode, which uses another technology from the Sigstore project. Fulcio is a code-signing certificate authority that generates short-lived certificates The advantage of this approach is that developers do not have to worry about key and certificate management themselves. The identity of the signer is ensured by the OpenID Connect (OIDC) protocol. For example, when Cosign makes a request to Fulcio to obtain a short-lived certificate, the user must log in to their GitHub or with an Google Account to authenticate. The user’s identity is stored within the certifate. Signatures should be checked by everyone, hence they are stored in a central location, called Rekor. Rekor is a transparency log, in which the digital signatures are appended. The entries can only be appended, but cannot be deleted or changed. To ensure this, Rekor uses Trillan. Trillan, in turn, is based on Merkle trees. The following figure shows how Developers can work with Sigstore:
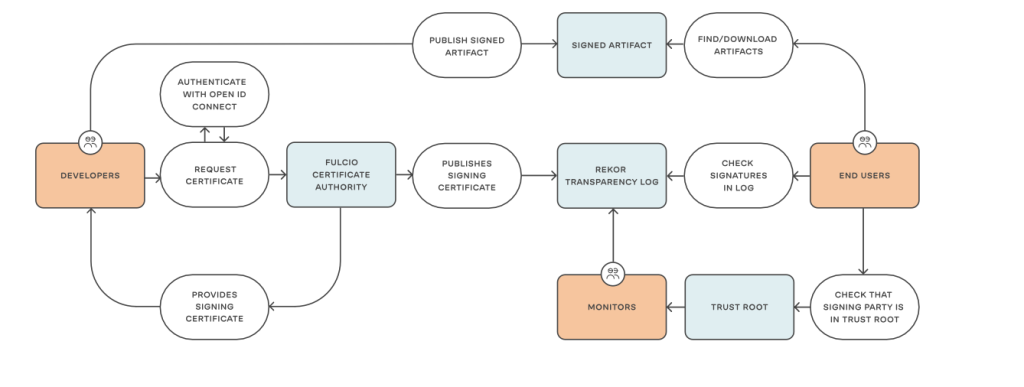
Developers can request a certificate from the Fulcio Certificate Authority. Authentication is doney with Open ID Connect. Develpers can then publish the Signed Artifact as well as the the Signing Certificate. On the other site, Developers, can find and download artifacts and check their signatures in the log.




