Introduction
With vRealize Automation, users can use existing load balancers as well as create load balancers within a deployment.
Before we show how to use existing load balancers or create new load balancers, let’s talk about the theory first.
Depending on the deployment type, different kind of load balancers are used. If you provision to a public cloud environment, vRealize Automation will create the appropriate load balancer (e.g. Elastic Load Balancer for Amazon AWS). If the deployment is for an on-premises environment and you have NSX properly set up, vRealize Automation will create NSX edges accordingly.
Features
The configuration is quite vendor-agnostic and provides the following features:
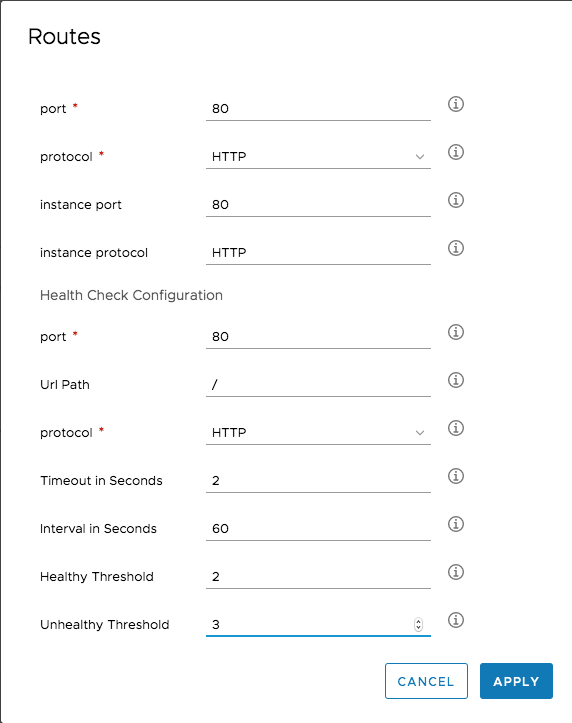
- HTTP, HTTPS, TCP and UDP ports can be used. When using HTTP or HTTPS, the load balancer operates at the request level (Layer 7), if you go for TCP or UDP, the load balancer operates at the connection level (Layer 4).
- In order to discover the availability of the instances, the load balancer supports health checks. This means , the load balancer periodically sends pings, attempts connections to test the virtual machines. When using HTTP for a health check, each virtual machine behind that is registered in the load balancer must respond with an HTTP status code 200. Otherwise, it will be consideres unhealthy. Health checks can also use other ports. When setting up TCP or UDP, an additional port has to be configured, to where a connection will be tried to be established. In addition, ICMP can also be used to periodically ping a machine.
- Health checks happen in intervals. When setting up a load balancer, you can specify the interval in seconds. In addition, you should set up an Unhealthy threshold, which is the number of continuous failed health checks before a load balancer machine is declared unhealthy. If a machine should be recognized as healthy again, a number of continuous successful health checks must be passed. This is called Healthy threshold. You can configure the Interval in seconds as well, which is the time between two load balancer health checks.
- Load balancer can be internet facing or internal – a property that can be configured on the blueprint.
That’s it. Next we will show how to use load balancers on blueprints.